DES
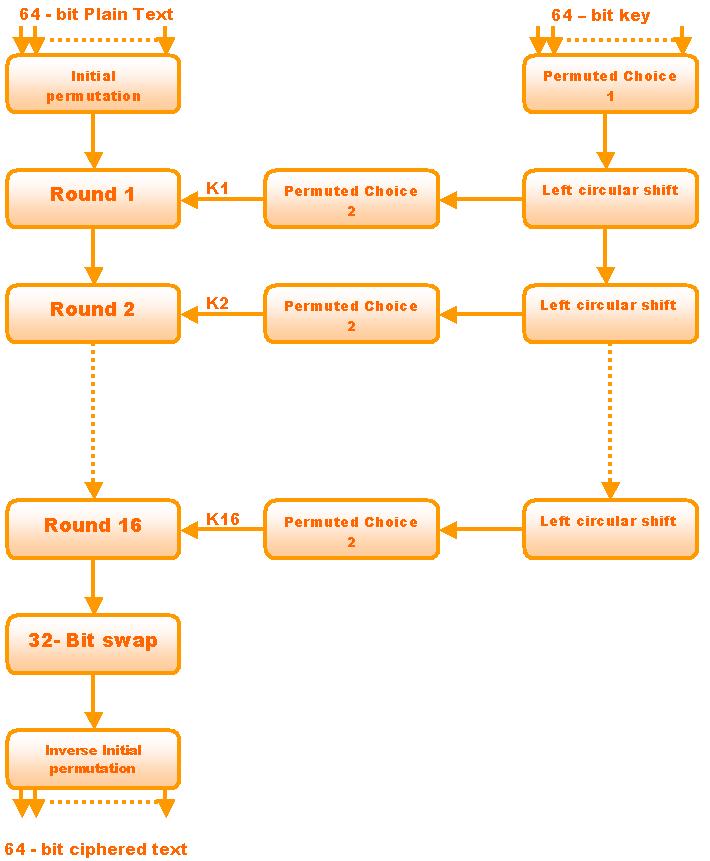
Figure : Depiction of DES Encryption Algorithm
Looking at the left-hand side of the figure , we can see that the processing of the plaintext proceeds in three phases. First, the 64-bit plain text passes through an initial permutation that rearranges the bits to produce the permuted input. This is followed by a phase consisting of 16 rounds of the same function, which involves both permutation and substitution functions. The output of the last (sixteenth)( round consists of 64 bits that are functions of the input plaintext and the key. The left and the right halves of the output are swapped to the preoutput. Finally, the preoutput is passed through a permutation that is the inverse of the initial permutation function to produce the 64-bit ciphertext.
Source : Cryptography and network security – William Stallings
The VHDL code of the above system was simulated and this is the Screenshot. The key and the plaintext were both '0', ciphertext is obtained after 16 clock cycles.
| First set of data: Key: 0000000000000000 (hex) Plaintext: 0000000000000000 (hex) |
| Expected ciphered text output: 8ca64de9c1b123a7 (hex) |
|
The pre layout DES standalone simulation results match the expected results. |