A "natural" candidate for emerging computer architectures is the concept of neuromorphic systems or computational networks constructed from neural networks. Neuromorphic computer architectures are inspired by biology in that their operation is based on our best understanding of the functionality of the mammalian brain. While artificial neural networks can be constructed from conventional electronic devices such as transistors, emerging nanoscale devices (e.g. memristors) exhibit properties particularly well suited for building high density, power-efficient neuromorphic systems. As part of our research, we are exploring how memristive devices can be exploited as synaptic elements in complex neural networks. This approach of "memristors as synapses" has been applied to several neuromorphic architectures, including brain-state-in-a-box (BSB) and popular Hopfield networks. Furthermore, in contrast to most silicon based reconfigurable devices, neuromorphic systems learn or are trained in much the same way as animals must learn. To this end, we are also engaged in the exploration of training methods for the memristor-based neuromorphic systems we design.
- C. Daffron, J. Chan, A. Disney, L. Bechtel, R. Wagner, M.E. Dean, G.S. Rose, J.S. Plank, J.D. Birdwell, and C.D. Schuman, “Extensions and Enhancements for the DANNA Neuromorphic Architecture,” in Proceedings of IEEE SoutheastCon, Norfolk, Virginia, March 2016.
- N.C. Cady, K. Beckmann, H. Manem, M.E. Dean, G.S. Rose, and J.E. Van Nostrand, “Towards Memristive Dynamic Adaptive Neural Network Arrays,” in Proceedings of the Government Microcircuit Applications and Critical Technology Conference (GOMACTech), Orlando, FL, March 2016.
- M. Hu, H. Li, Y. Chen, Q. Wu, G. S. Rose, and R. Linderman, “Memristor Crossbar-Based Neuromorphic Computing System: A Case Study,” IEEE Transactions on Neural Networks and Learning Systems, vol. 25, no. 10, pp. 1864—1878, October 2014. (DOI: 10.1109/TNNLS.2013.2296777)
- M. Soltiz, D. Kudithipudi, C. Merkel, G. S. Rose, and R. E. Pino, “Memristor-Based Neural Logic Blocks for Nonlinearly Separable Functions,” IEEE Transactions on Computers, vol. 62, no. 8, pp. 1597—1606, August 2013. (DOI: 10.1109/TC.2013.75)
Nano-enabled Hardware Security
As is the case with any modern computing system, nanoelectronic architectures must be designed and implemented with special attention paid to potential security concerns. For example, a hardware encryption engine can be designed to provide high security encryption but if not implemented properly information leakage via side-channels (e.g. power) can be exploited by malicious parties to retrieve sensitive information. Side-channel attacks have emerged as a serious concern for computer systems and even strong encryption techniques such as AES can be susceptible to leaky side-channels if the overall system is not designed properly. Recent work in this area includes the design and simulation of a memristor-based system that minimizes the likelihood of a side-channel attack by leveraging the reconfigurability and inherent process variations of memristors.
Hardware security is also concerned with issues such as counterfeiting and design piracy where malicious parties could enter the supply chain for integrated circuits. One popular solution explored by many research groups for combating hardware security concerns is the use of a physical unclonable function (PUF) that can provide unique "fingerprints" for integrated circuits or be used to generate secret keys. A PUF leverages the inherent process variations of an integrated circuit (typically bad news) to generate digital responses that are unique to a particular device implementation. Nanoelectronic PUF circuits have been designed that leverage process variations in properties such as the write-time of memristive devices. More specifically, when driving a write pulse across several memristors simultaneously we have shown that some of the devices will switch and some will not. A unique PUF response can then be generated based on which memristive devices switch. The construction of hardware security primitives from nanoscale devices such as memristors is expected to lead to secure hardware with a small footprint and low power consumption.
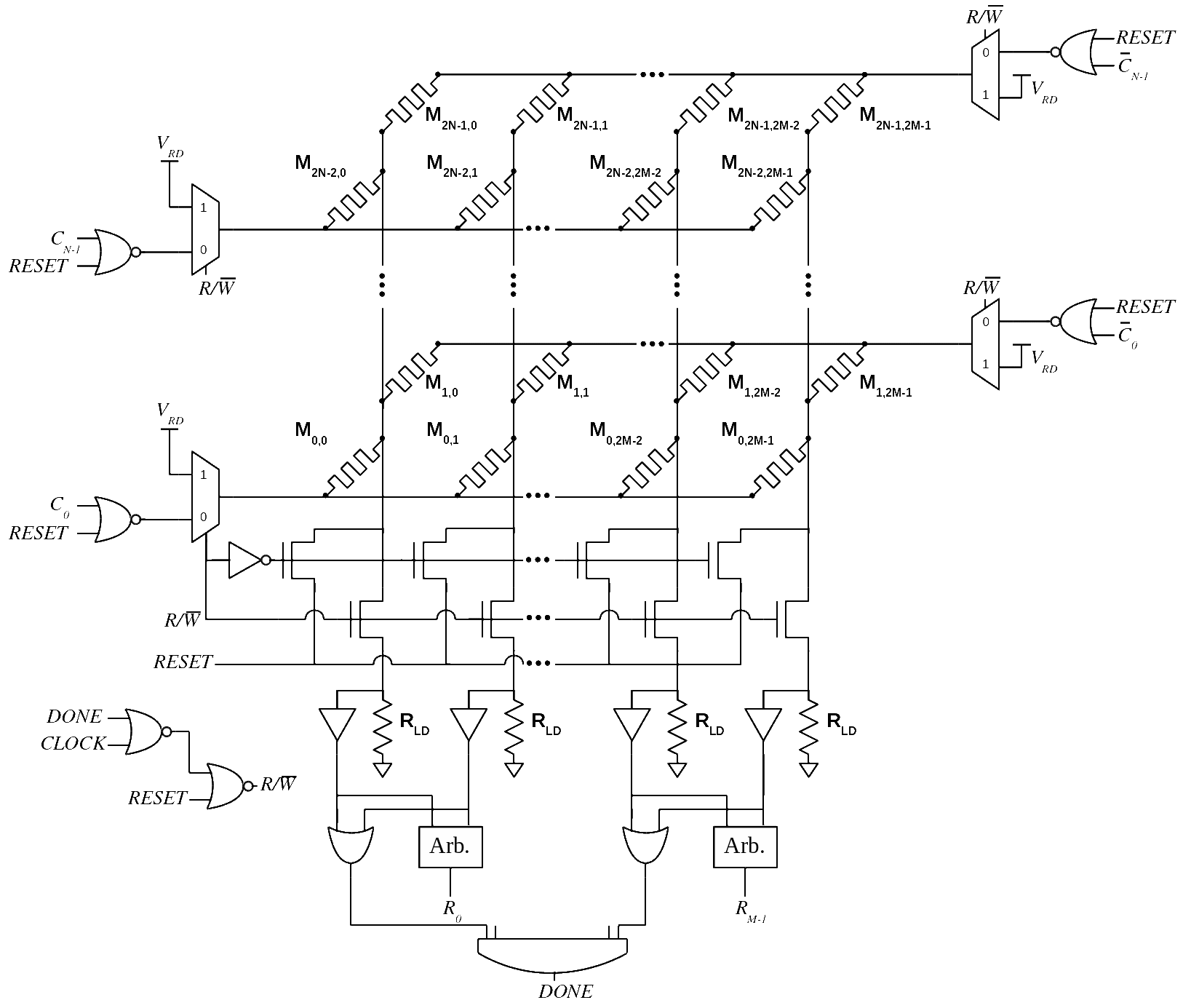
Example of a memristive crossbar-based physical unclonable function (PUF).
- J. Bohl, L.-K. Yan, and G. S. Rose, “A Two-Dimensional Chaotic Logic Gate for Improved Computer Security,” in Proceedings of Midwest Symposium on Circuits and Systems (MWSCAS), Fort Collins, CO, August 2015. (DOI: 10.1109/MWSCAS.2015.7282078)
- G. S. Rose and C. A. Meade, “Performance Analysis of a Memristive Crossbar PUF Design,” in Proceedings of Design Automation Conference (DAC), San Francisco, CA, June 2015. (DOI: 10.1145/2744769.2744892)
- J. Rajendran, R. Karri, M. Potkonjak, N. McDonald, G. S. Rose, and B. Wysocki, “Nano Meets Security: Exploring Nanoelectronic Devices for Security Applications,” Proceedings of the IEEE, vol. 103, no.5, pp. 829—849, May 2015. (DOI: 10.1109/JPROC.2014.2387353)
- J. Rajendran, H. Zhang, C. Zhang, G. S. Rose, Y. Pino, O. Sinanoglu, and R. Karri, “Fault Analysis-based Logic Encryption,” IEEE Transactions on Computers, vol. 64, no. 2, pp. 410—424, February 2015. (DOI: 10.1109/TC.2013.193)
- G. Khedkar, D. Kudithipudi, and G. S. Rose, “Power Profile Obfuscation using Nanoscale Memristive Devices to Counter DPA Attacks,” IEEE Transactions on Nanotechnology, vol. 14, no. 1, pp. 26 – 35, January 2015. (DOI: 10.1109/TNANO.2014.2362416)
Memristor Device Modeling and Simulation
Designing and simulating nanelectronic circuits built from novel devices requires accurate models that reflects the expected behavior of those devices. As the nanelectronic devices we explore tend to be experimental, industry tested device models do not typically exist. Thus, device models must be developed based on our best understanding of device behavior. Several memristor device models have actually been developed and presented in scientific literature from which one can begin when designing memristor-based circuits. However, memristors, like most nanoelectronic devices, are still experimental such that the models require regular refinement.
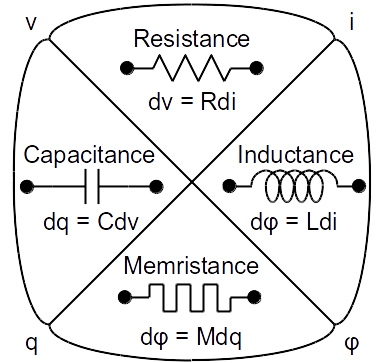
The memristor as the fourth fundamental circuit element.
- S. Amer, S. Sayyaparaju, K. Beckmann, N.C. Cady, and G.S. Rose, “A Practical Hafnium-Oxide Memristor Model Suitable for Circuit Design and Simulation,” to appear in Proceedings of IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, May 2017.
- G. S. Rose, “Overview: Memristive Devices, Circuits and Systems,” in Proceedings of the IEEE International Symposium on Circuits and Systems, Paris, France, June 2010. (special session)
- G. S. Rose, M. M. Ziegler, and M. R. Stan, “A Large-Signal Universal Device Model for Nanoelectronic Circuit Simulation,” IEEE Transactions on Very Large Scale Integration, vol. 12, no. 11, pp. 1201—1208, Nov. 2004.
- M. M. Ziegler, G. S. Rose, and M. R. Stan, “A Universal Device Model for Nanoelectronic Circuit Simulation,” in Proceedings of the 2nd IEEE Conference on Nanotechnology, Washington, D.C., August 2002, pp. 83–88.
Nanoelectronic Circuit Design for Emerging Computing Architectures
The field of nanoelectronics is often defined as being concerned with any technology whose feature sizes are on the order of just a few nanometers (1×10-9 meters). Many in the field have performed experiments that have shown how such devices could be fabricated with useful properties such as recitification, hysteresis, and negative differential resistance (NDR). Our work in this regard focuses on the uses of such novel devices for the implementation of computer architectures whose behavior often deviates from that of traditional designs. In the past this has even included exploring ways to building computers from organic molecules. To date, our research has led to low-level design techniques for implementing nanoscale electronic circuits. Our circuit-level approach (taking actual experimental data to build up device models) has led to molecular electronic programmable logic circuits, neuromorphic systems and nanoelectronic hardware security primitives. By leveraging the often exotic behavior of nanoelectronic devices this research aims to develop new computer architectures that are smaller, more cost effective and less power hungry as compared to traditional systems.
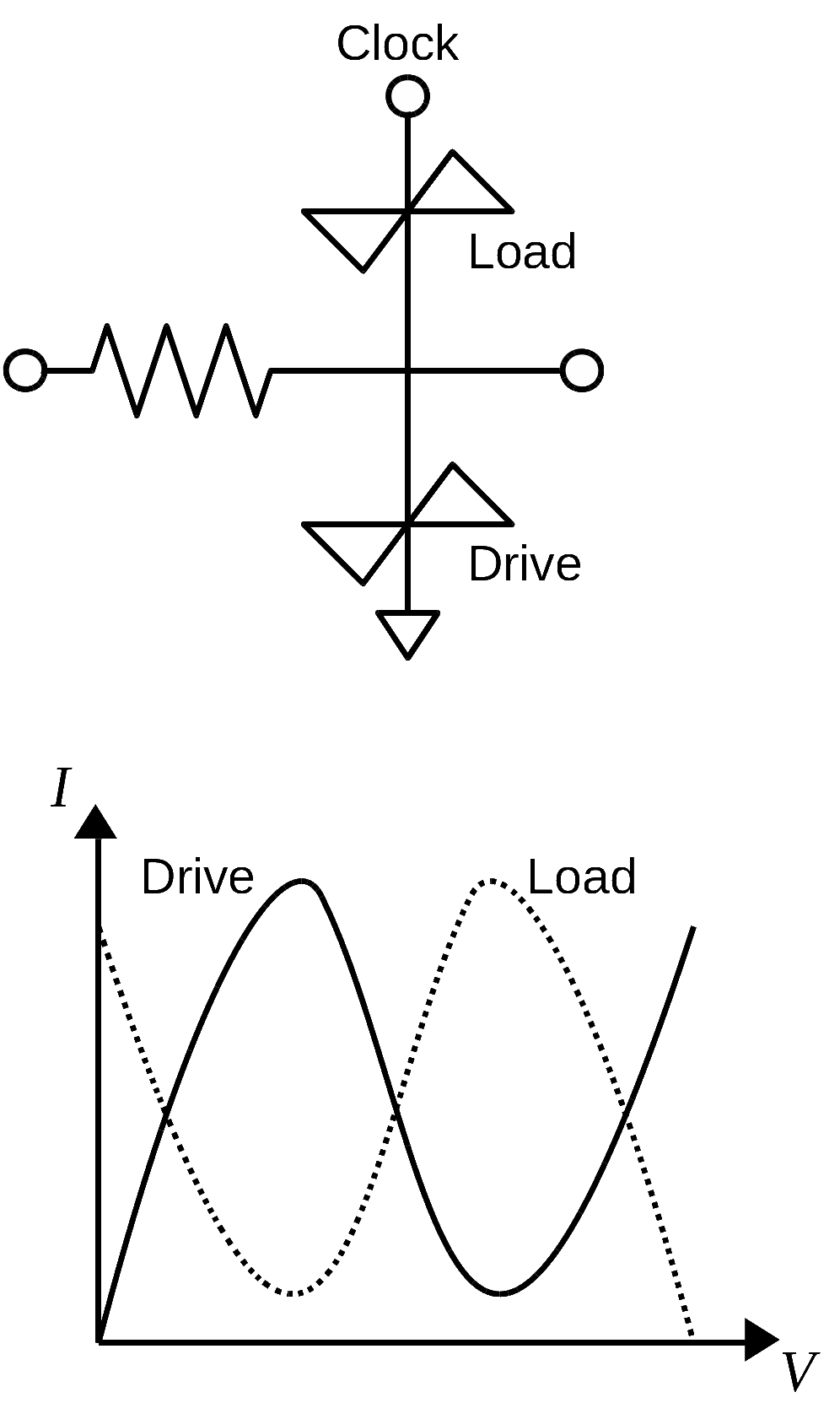
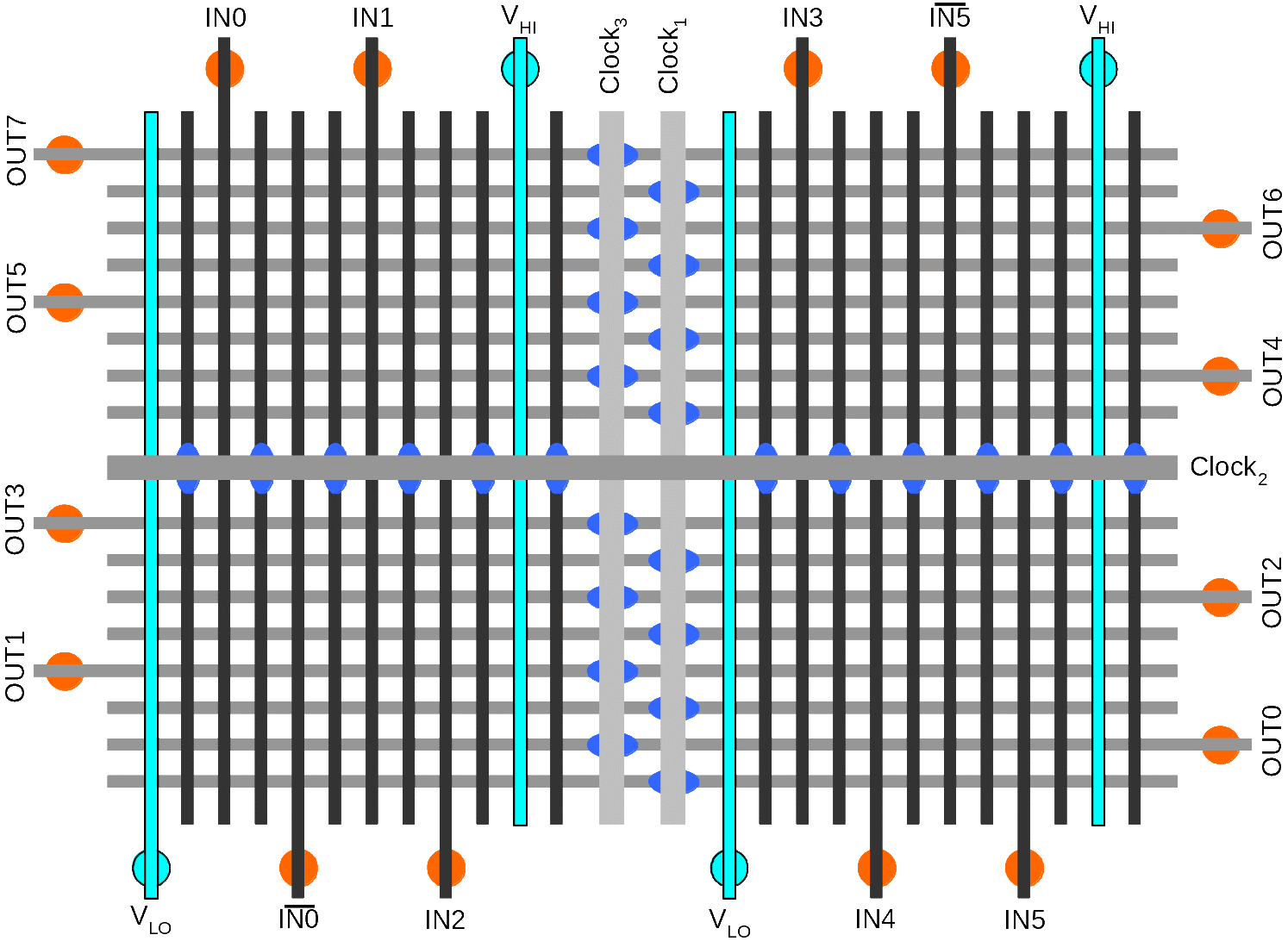
Example of a nanoelectronic architecture: the programmable majority logic array (right) built from NDR-based Goto pair circuits (top-left).
- G. S. Rose, H. Manem, J. Rajendran, R. Karri, and R. Pino, “Leveraging Memristive Systems in the Construction of Digital Logic Circuits,” Proceedings of the IEEE, vol. 100, no. 6, June 2012. (DOI: 10.1109/JPROC.2011.2167489)
- B. Gojman, H. Manem, G. S. Rose, and A. DeHon, “Inversion Schemes for Sublithographic Programmable Logic Arrays,” IET Computers & Digital Techniques, vol. 3, no. 6, pp. 625—642, Nov. 2009. (DOI: 10.1049/iet-cdt.2008.0128)
- G. S. Rose and M. R. Stan, “A Programmable Majority Logic Array using Molecular Scale Electronics,” IEEE Trans. Circuits Syst. I, vol. 54, no. 11, pp. 2380–2390, Nov. 2007.



